Most environments used to use the Integrated Windows Authentication (IWA) as an identity source for vCenter. However with Microsoft tightening the screw on LDAP signing and VMware deprecating IWA in versions 7 and above, many will have to bite the bullet and move to LDAPS.
It’s not a big deal to set up, it will however add some administrative overhead whenever a domain controller is expired, replaced or a new DC is added. Note that the permissions will be persisted if you are moving from IWA so you won’t need to recreate them. You can delete the IWA identity source and add the LDAPS one.
This blog is an extract of a blog written for Altaro Software, you can find the full length article here. Let’s go through the steps :
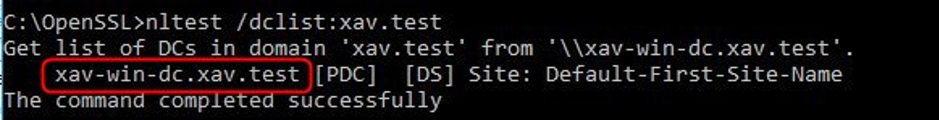
1. List the domain controllers in the domain that should be the identity source.
nltest /dclist:xav.test
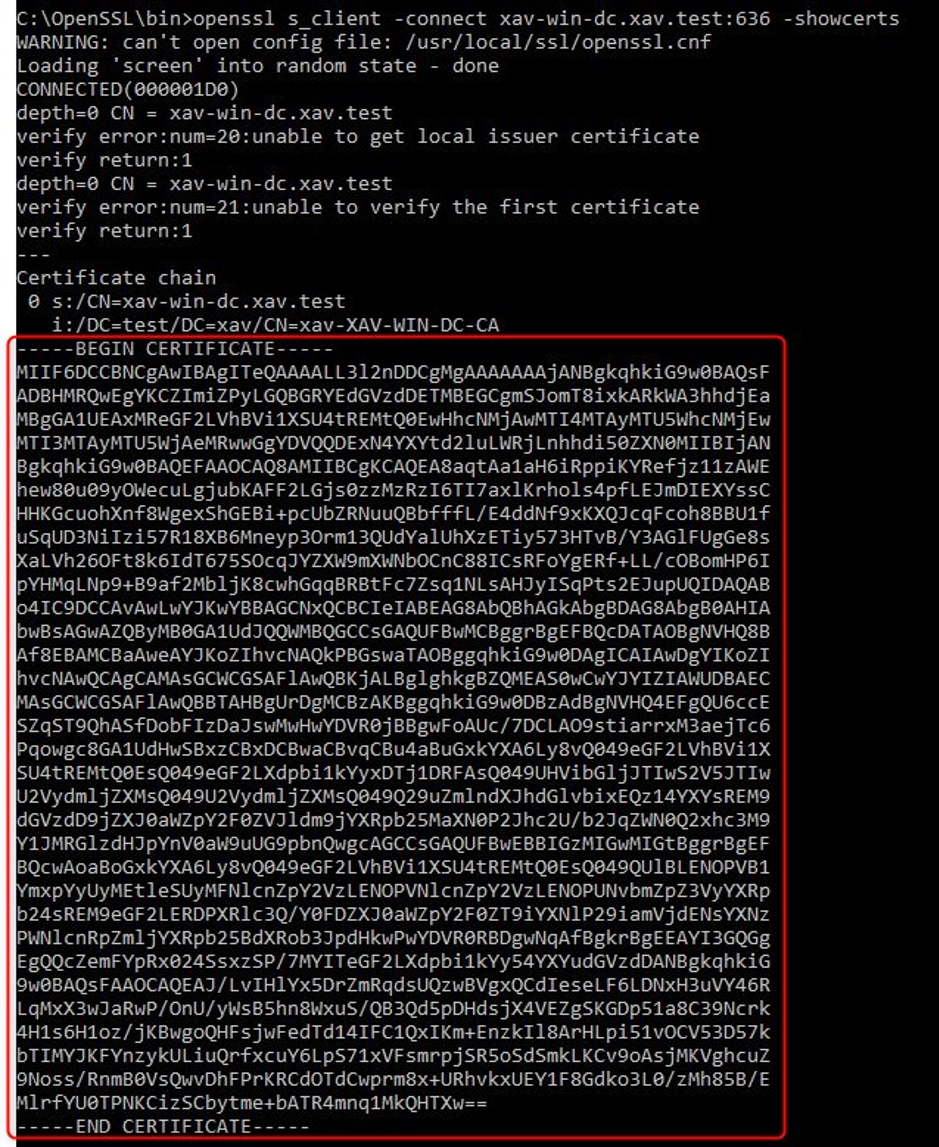
2. Run this command against each domain controller to retrieve their certificates and store them in .cer files.
openssl s_client -connect xav-win-dc.xav.test:636 -showcerts
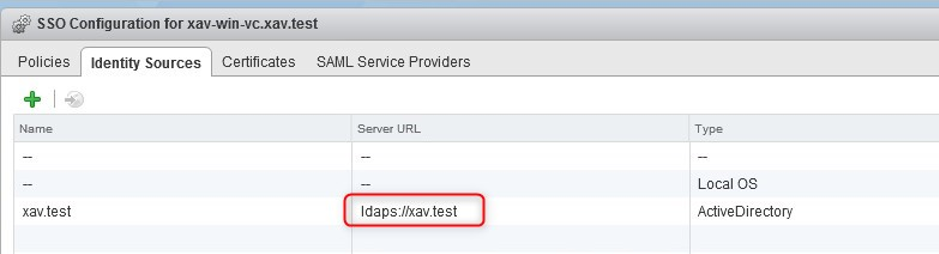
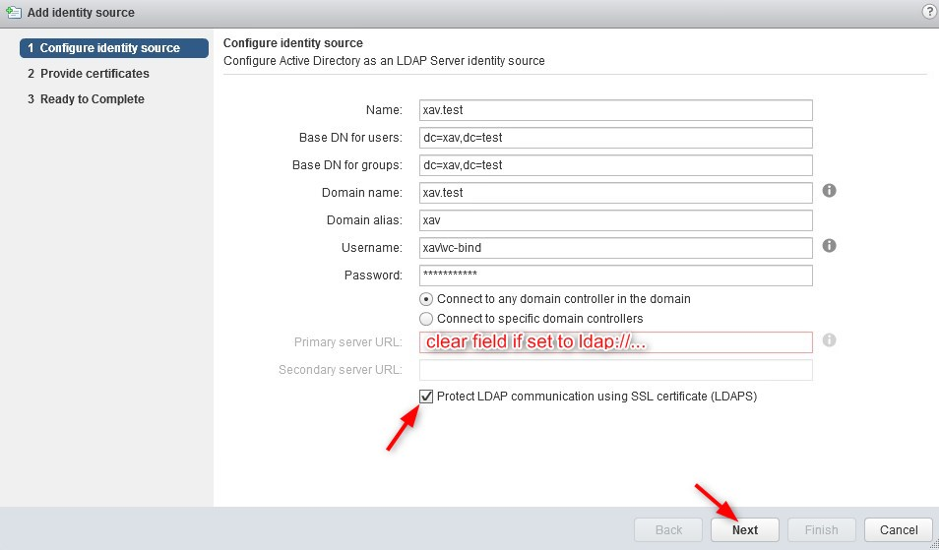
3. Log in vCenter using an SSO admin ([email protected]) > Administration > Configuration > Identity sources.
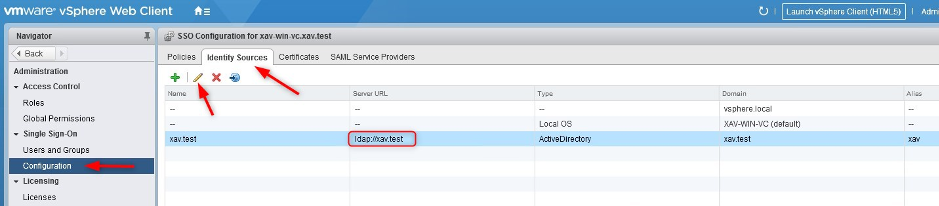
4. Edit or create an LDAP source > Enable LDAPs on the identity source by checking “Protect LDAP communication using SSL certificate (LDAPS)” and click “Next”.
If you have an existing ldap source, clear the primary server url field or it will incorrectly show ldap instead of ldaps even after the change.
5. Add each DC certificate in the list.
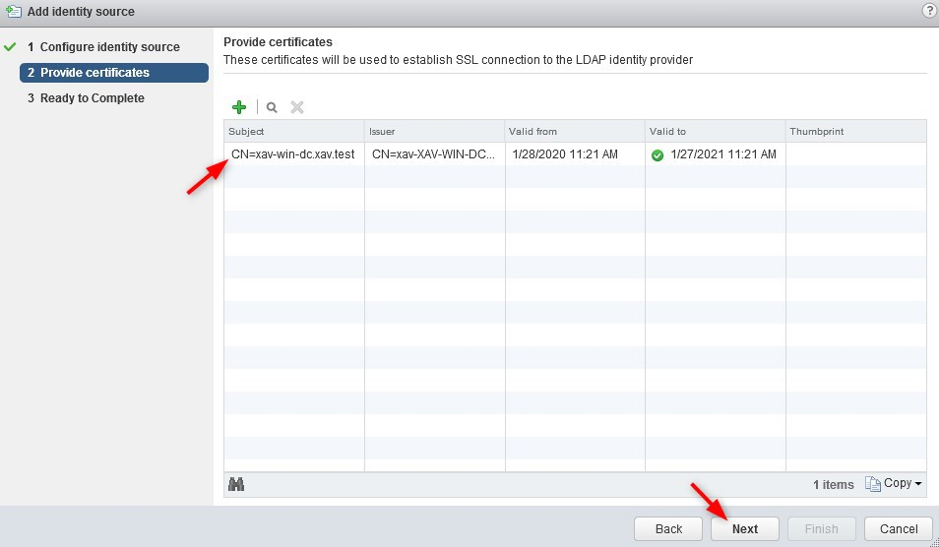
The identity source should now show ldaps.